Users, Privileges, and Roles
This topic provides an overview of Role-Based Access Control (RBAC) in Milvus, detailing the definitions and relationships between users, roles, objects, and privileges.
The following figure illustrates the relationship between objects, privileges, roles, and users.
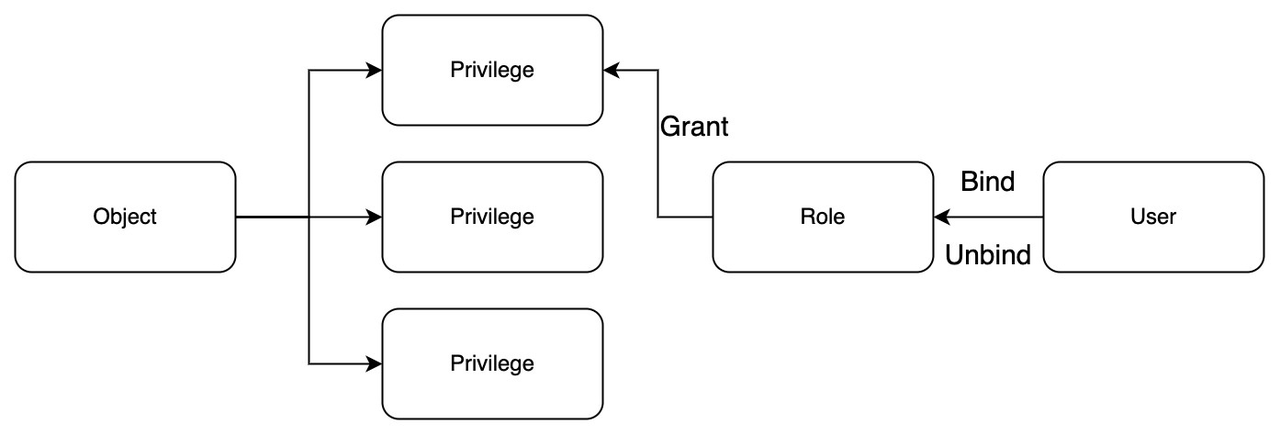 users_and_roles
users_and_roles
Key concepts
To manage access control to Milvus resources, it’s important to understand the key components of RBAC: object types, object names, users, roles, and privileges.
Object type: the category of the object for which a privilege is being assigned. The object type can be:
Global: System-wide objects, allowing the user to perform actions that affect all collections, users, or system-wide settings.Collection: Collection-specific objects, allowing the user to perform actions such as creating indexes, loading data, inserting or deleting data, and querying data within a specific collection.User: Objects related to user management, allowing the user to manage credentials and roles for database users, such as updating user credentials or viewing user details.
Object name: the specific name of the object to control access for. For instance:
- If the object type is
Global, the object name must be set to the wildcard (*), indicating all objects of the specified type. - If the object type is
Collection, the object name is the name of a collection. - If the object type is
User, the object name is the name of a database user.
- If the object type is
User: a person or an application that interacts with Milvus, which consists of a username and a corresponding password.
Privilege: defines the actions that can be performed and the resources that can be accessed. Privileges are not granted directly to users but are assigned to roles.
Role: defines the set of privileges that a user has for certain objects. Once a role is bound to a user, the user inherits all the privileges granted to that role.
Example: Granting privileges
The following code snippet shows how to grant a CreateIndex privilege to a role on a specific collection:
milvusClient.grant_privilege(
role_name="CUSTOM_ROLE_NAME",
object_type="Collection", # Valid value: Global, Collection or User.
privilege="CreateIndex", # See the table below for valid privilege names and relevant API descriptions.
object_name="YOUR_COLLECTION_NAME" # The name of the collection to grant access to. Use "*" to grant access to all collections.
)
GrantPrivilegeReq grantPrivilegeReq = GrantPrivilegeReq.builder()
.roleName("roleName")
.objectName("CollectionName") // The name of the collection to grant access to. Use "*" to grant access to all collections.
.objectType("Collection") // Valid value: Global, Collection or User.
.privilege("CreateIndex") // See the table below for valid privilege names and relevant API descriptions.
.build();
client.grantPrivilege(grantPrivilegeReq);
milvusClient.grantPrivilege({
roleName: 'roleName',
object: 'Collection', // Valid value: Global, Collection or User.
objectName: 'CollectionName', // The name of the collection to grant access to. Use "*" to grant access to all collections.
privilegeName: 'CreateIndex' // See the table below for valid privilege names and relevant API descriptions.
})
To obtain more information about privilege-related APIs, refer to grant_privilege and revoke_privilege.
To obtain more information about privilege-related APIs, refer to grantPrivilege and revokePrivilege.
To obtain more information about privilege-related APIs, refer to grantPrivilege and revokePrivilege.
Default users and roles
Milvus creates a root user by default with a default password Milvus. The root user is granted the admin privileges, which means that this root user can have access to all resources and perform all actions.
If a user is associated with the public role, they are entitled to the following privileges:
DescribeCollectionShowCollectionsIndexDetail
List of object types and privileges
The following table lists the values you can choose when enabling RBAC.
| Object type | Privilege name | Relevant API description on the client side |
|---|---|---|
| Collection | CreateIndex | CreateIndex |
| Collection | DropIndex | DropIndex |
| Collection | IndexDetail | DescribeIndex/GetIndexState/GetIndexBuildProgress |
| Collection | Load | LoadCollection/GetLoadingProgress/GetLoadState |
| Collection | GetLoadingProgress | GetLoadingProgress |
| Collection | GetLoadState | GetLoadState |
| Collection | Release | ReleaseCollection |
| Collection | Insert | Insert |
| Collection | Delete | Delete |
| Collection | Upsert | Upsert |
| Collection | Search | Search |
| Collection | Flush | Flush/GetFlushState |
| Collection | GetFlushState | GetFlushState |
| Collection | Query | Query |
| Collection | GetStatistics | GetCollectionStatistics |
| Collection | Compaction | Compact |
| Collection | Import | BulkInsert/Import |
| Collection | LoadBalance | LoadBalance |
| Collection | CreatePartition | CreatePartition |
| Collection | DropPartition | DropPartition |
| Collection | ShowPartitions | ShowPartitions |
| Collection | HasPartition | HasPartition |
| Global | All | All API operation permissions in this table |
| Global | CreateCollection | CreateCollection |
| Global | DropCollection | DropCollection |
| Global | DescribeCollection | DescribeCollection |
| Global | ShowCollections | ShowCollections |
| Global | RenameCollection | RenameCollection |
| Global | FlushAll | FlushAll |
| Global | CreateOwnership | CreateUser CreateRole |
| Global | DropOwnership | DeleteCredential DropRole |
| Global | SelectOwnership | SelectRole/SelectGrant |
| Global | ManageOwnership | OperateUserRole OperatePrivilege |
| Global | CreateResourceGroup | CreateResourceGroup |
| Global | DropResourceGroup | DropResourceGroup |
| Global | DescribeResourceGroup | DescribeResourceGroup |
| Global | ListResourceGroups | ListResourceGroups |
| Global | TransferNode | TransferNode |
| Global | TransferReplica | TransferReplica |
| Global | CreateDatabase | CreateDatabase |
| Global | DropDatabase | DropDatabase |
| Global | ListDatabases | ListDatabases |
| Global | CreateAlias | CreateAlias |
| Global | DropAlias | DropAlias |
| Global | DescribeAlias | DescribeAlias |
| Global | ListAliases | ListAliases |
| User | UpdateUser | UpdateCredential |
| User | SelectUser | SelectUser |
What’s next
- Learn how to enable RBAC.