Create Privilege Group
To streamline the process of granting privileges, it is recommended that you combine multiple privileges into a privilege group.
Privilege group vs. privileges
A privilege group consists of multiple privileges.
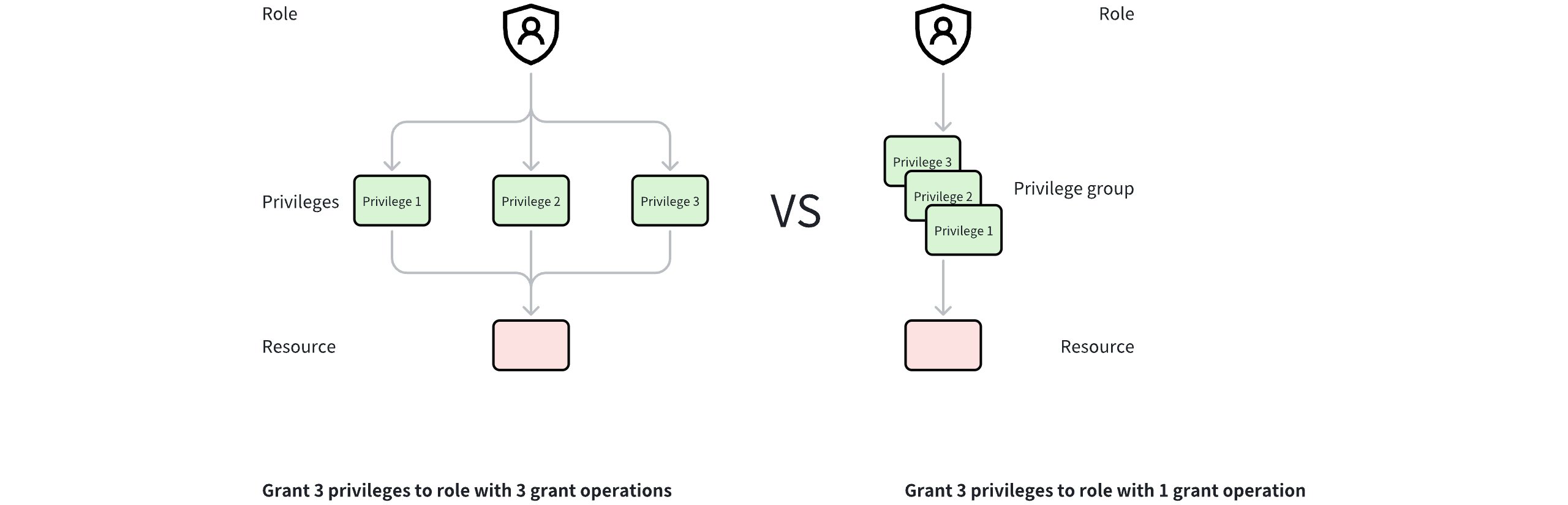 Privilege Group Illustrated
Privilege Group Illustrated
As shown in the figure above, suppose you need to grant three different privileges to a role.
If you do not use a privilege group, you need to grant the privileges three times.
If you use a privilege group, you only need to create a privilege group and add the three privileges to this privilege group and grant the privilege group to Role A.
By using a privilege group, you can grant multiple privileges in bulk to a role.
Built-in privilege groups
For ease-of-use, Milvus provides a total of 9 built-in privileges on the collection, database, and instance level: COLL_RO, COLL_RW, COLL_ADMIN, DB_RO, DB_RW, DB_Admin, Cluster_RO, Cluster_RW and Cluster_Admin.
The three levels of built-in privilege groups do not have a cascading relationship. Setting a privilege group at the instance level does not automatically set permissions for all databases and collections under that instance. Privileges at the database and collection levels need to be set manually.
The following tables explains the privileges includes in each of the built-in privilege group.
Collection level
CollectionReadOnly (COLL_RO): includes privileges to read collection data
CollectionReadWrite (COLL_RW): includes privileges to read and write collection data
CollectionAdmin (COLL_ADMIN): includes privileges to read and write collection data and manage collections.
The table below lists the specific privileges included in the three built-in privilege groups at the collection level:
Privilege |
CollectionReadOnly |
CollectionReadWrite |
CollectionAdmin |
|---|---|---|---|
Query |
✔️ |
✔️ |
✔️ |
Search |
✔️ |
✔️ |
✔️ |
IndexDetail |
✔️ |
✔️ |
✔️ |
GetFlushState |
✔️ |
✔️ |
✔️ |
GetLoadState |
✔️ |
✔️ |
✔️ |
GetLoadingProgress |
✔️ |
✔️ |
✔️ |
HasPartition |
✔️ |
✔️ |
✔️ |
ShowPartitions |
✔️ |
✔️ |
✔️ |
ListAliases |
✔️ |
✔️ |
✔️ |
DescribeCollection |
✔️ |
✔️ |
✔️ |
DescribeAlias |
✔️ |
✔️ |
✔️ |
GetStatistics |
✔️ |
✔️ |
✔️ |
CreateIndex |
❌ |
✔️ |
✔️ |
DropIndex |
❌ |
✔️ |
✔️ |
CreatePartition |
❌ |
✔️ |
✔️ |
DropPartition |
❌ |
✔️ |
✔️ |
Load |
❌ |
✔️ |
✔️ |
Release |
❌ |
✔️ |
✔️ |
Insert |
❌ |
✔️ |
✔️ |
Delete |
❌ |
✔️ |
✔️ |
Upsert |
❌ |
✔️ |
✔️ |
Import |
❌ |
✔️ |
✔️ |
Flush |
❌ |
✔️ |
✔️ |
Compaction |
❌ |
✔️ |
✔️ |
LoadBalance |
❌ |
✔️ |
✔️ |
CreateAlias |
❌ |
❌ |
✔️ |
DropAlias |
❌ |
❌ |
✔️ |
Database level
DatabaseReadOnly (DB_RO): includes privileges to read database data
DatabaseReadWrite (DB_RW): includes privileges to read and write database data
DatabaseAdmin (DB_Admin): includes privileges to read and write database data and manage databases.
The table below lists the specific privileges included in the three built-in privilege groups at the database level:
Privilege |
DatabaseReadOnly |
DatabaseReadWrite |
DatabaseAdmin |
|---|---|---|---|
ShowCollections |
✔️ |
✔️ |
✔️ |
DescribeDatabase |
✔️ |
✔️ |
✔️ |
CreateCollection |
✔️ |
✔️ |
✔️ |
DropCollection |
❌ |
❌ |
✔️ |
AlterDatabase |
❌ |
✔️ |
✔️ |
Cluster level
ClusterReadOnly (Cluster_RO): includes privileges to read instance data
ClusterReadWrite (Cluster_RW): includes privileges to read and write instance data
ClusterAdmin (Cluster_Admin): includes privileges to read and write instance data and manage instances.
The table below lists the specific privileges included in the three built-in privilege groups at the instance level:
Privilege |
ClusterReadOnly |
ClusterReadWrite |
ClusterAdmin |
|---|---|---|---|
ListDatabases |
✔️ |
✔️ |
✔️ |
RenameCollection |
❌ |
❌ |
✔️ |
CreateOwnership |
❌ |
❌ |
✔️ |
UpdateUser |
❌ |
❌ |
✔️ |
DropOwnership |
❌ |
❌ |
✔️ |
SelectOwnership |
✔️ |
✔️ |
✔️ |
ManageOwnership |
❌ |
❌ |
✔️ |
SelectUser |
✔️ |
✔️ |
✔️ |
BackupRBAC |
❌ |
❌ |
✔️ |
RestoreRBAC |
❌ |
❌ |
✔️ |
CreateResourceGroup |
❌ |
❌ |
✔️ |
DropResourceGroup |
❌ |
❌ |
✔️ |
UpdateResourceGroups |
❌ |
✔️ |
✔️ |
DescribeResourceGroup |
✔️ |
✔️ |
✔️ |
ListResourceGroups |
✔️ |
✔️ |
✔️ |
TransferNode |
❌ |
✔️ |
✔️ |
TransferReplica |
❌ |
✔️ |
✔️ |
CreateDatabase |
❌ |
❌ |
✔️ |
DropDatabase |
❌ |
❌ |
✔️ |
FlushAll |
❌ |
✔️ |
✔️ |
CreatePrivilegeGroup |
❌ |
❌ |
✔️ |
DropPrivilegeGroup |
❌ |
❌ |
✔️ |
ListPrivilegeGroups |
❌ |
❌ |
✔️ |
OperatePrivilegeGroup |
❌ |
❌ |
✔️ |
Procedures
You can create a privilege group and then add privileges to the privilege group.
Create a privilege group
The following example demonstrates how to create a privilege group named privilege_group_1.
from pymilvus import MilvusClient
client.create_privilege_group(group_name='privilege_group_1')
import "github.com/milvus-io/milvus/client/v2/milvusclient"
err = client.CreatePrivilegeGroup(ctx, milvusclient.NewCreatePrivilegeGroupOption("privilege_group_1"))
if err != nil {
fmt.Println(err.Error())
// handle error
}
import io.milvus.v2.service.rbac.request.CreatePrivilegeGroupReq;
client.createPrivilegeGroup(CreatePrivilegeGroupReq.builder()
.groupName("privilege_group_1")
.build());
await client.createPrivilegeGroup({
group_name: 'privilege_group_1',
});
curl --request POST \
--url "${CLUSTER_ENDPOINT}/v2/vectordb/privilege_groups/create" \
--header "Authorization: Bearer ${TOKEN}" \
--header "Content-Type: application/json" \
-d '{
"privilegeGroupName":"privilege_group_1"
}'
Add privileges to a privilege group
The following example demonstrates how to add privileges PrivilegeBackupRBAC and PrivilegeRestoreRBAC to the privilege group privilege_group_1 that is just created.
from pymilvus import MilvusClient
client.add_privileges_to_group(group_name='privilege_group_1', privileges=['Query', 'Search'])
import "github.com/milvus-io/milvus/client/v2/milvusclient"
privileges := []string{"Query", "Search"}
err = client.AddPrivilegesToGroup(ctx, milvusclient.NewAddPrivilegesToGroupOption("privilege_group_1", privileges...))
if err != nil {
fmt.Println(err.Error())
// handle error
}
import io.milvus.v2.service.rbac.request.AddPrivilegesToGroupReq;
client.addPrivilegesToGroup(AddPrivilegesToGroupReq.builder()
.groupName("privilege_group_1")
.privileges(Arrays.asList("Query", "Search"))
.build());
await client.addPrivilegesToGroup({
group_name: privilege_group_1,
privileges: ['Query', 'Search'],
});
curl --request POST \
--url "${CLUSTER_ENDPOINT}/v2/vectordb/privilege_groups/add_privileges_to_group" \
--header "Authorization: Bearer ${TOKEN}" \
--header "Content-Type: application/json" \
-d '{
"privilegeGroupName":"privilege_group_1",
"privileges":["Query", "Search"]
}'
Remove privileges from a privilege group
The following example demonstrates how to remove the privilege PrivilegeRestoreRBAC from the privilege group privilege_group_1.
from pymilvus import MilvusClient
client.remove_privileges_from_group(group_name='privilege_group_1', privileges='Search')
import "github.com/milvus-io/milvus/client/v2/milvusclient"
err = client.RemovePrivilegesFromGroup(ctx, milvusclient.NewRemovePrivilegesFromGroupOption("privilege_group_1", []string{"Search"}...))
if err != nil {
fmt.Println(err.Error())
// handle error
}
import io.milvus.v2.service.rbac.request.RemovePrivilegesFromGroupReq;
client.removePrivilegesFromGroup(RemovePrivilegesFromGroupReq.builder()
.groupName("privilege_group_1")
.privileges(Collections.singletonList("Search"))
.build());
await client.removePrivilegesFromGroup({
group_name: "privilege_group_1",
privileges: ["Search"],
});
curl --request POST \
--url "${CLUSTER_ENDPOINT}/v2/vectordb/privilege_groups/remove_privileges_from_group" \
--header "Authorization: Bearer ${TOKEN}" \
--header "Content-Type: application/json" \
-d '{
"privilegeGroupName":"privilege_group_1",
"privileges":["Search"]
}'
List privilege groups
The following example demonstrates how to list all existing privilege groups.
from pymilvus import MilvusClient
client.list_privilege_groups()
import "github.com/milvus-io/milvus/client/v2/milvusclient"
groups, err := client.ListPrivilegeGroups(ctx, milvusclient.NewListPrivilegeGroupsOption())
if err != nil {
fmt.Println(err.Error())
// handle error
}
import io.milvus.v2.service.rbac.PrivilegeGroup;
import io.milvus.v2.service.rbac.request.ListPrivilegeGroupsReq;
import io.milvus.v2.service.rbac.response.ListPrivilegeGroupsResp;
ListPrivilegeGroupsResp resp = client.listPrivilegeGroups(ListPrivilegeGroupsReq.builder()
.build());
List<PrivilegeGroup> groups = resp.getPrivilegeGroups();
await client.listPrivilegeGroups();
curl --request POST \
--url "${CLUSTER_ENDPOINT}/v2/vectordb/privilege_groups/list" \
--header "Authorization: Bearer ${TOKEN}" \
--header "Content-Type: application/json" \
-d '{}'
Below is an example output.
PrivilegeGroupItem: <privilege_group:privilege_group_1>, <privileges:('Search', 'Query')>
Drop a privilege group
The following example demonstrates how to drop the privilege group privilege_group_1.
from pymilvus import MilvusClient
client.drop_privilege_group(group_name='privilege_group_1')
import "github.com/milvus-io/milvus/client/v2/milvusclient"
err = client.DropPrivilegeGroup(ctx, milvusclient.NewDropPrivilegeGroupOption("privilege_group_1"))
if err != nil {
fmt.Println(err.Error())
// handle error
}
import io.milvus.v2.service.rbac.request.DropPrivilegeGroupReq;
client.dropPrivilegeGroup(DropPrivilegeGroupReq.builder()
.groupName("privilege_group_1")
.build());
await client.dropPrivilegeGroup({group_name: 'privilege_group_1'});
curl --request POST \
--url "${CLUSTER_ENDPOINT}/v2/vectordb/privilege_groups/drop" \
--header "Authorization: Bearer ${TOKEN}" \
--header "Content-Type: application/json" \
-d '{
"privilegeGroupName":"privilege_group_1"
}'